URGENT ANNOUNCEMENT
For your safety, we inform you that there is an ongoing attempt to spread malicious software through misleading email messages (phishing) that are supposedly sent by WebHotelier.
More specifically, messages containing booking confirmations are being sent which contain links that lead to the download of malicious software (executable files .exe) instead of booking printouts (PDFs).
Attack Details:
Compromised computers or servers running inside hotels are used as the attack vector. The malicious person or persons are using those compromised systems to send emails to other hoteliers.
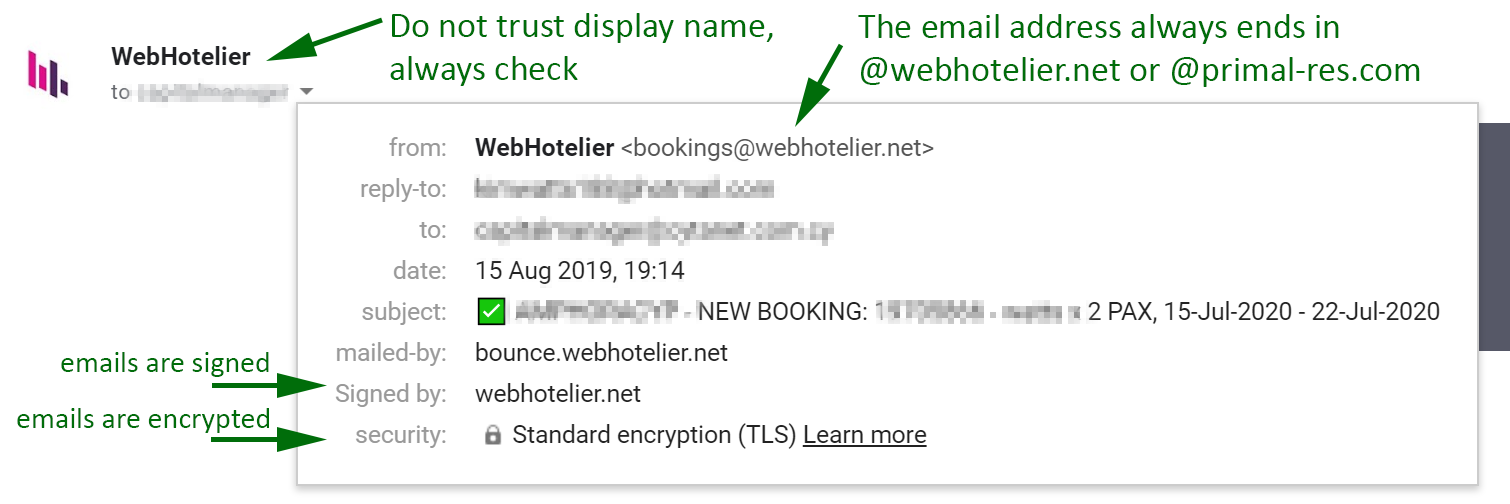
A phishing email used in the attack looks like this:

Why is this attack dangerous?
Most serious email providers and email servers can protect you from many phishing attempts. However, this attack is more dangerous than normal because compromised hotel servers are being used. The malicious agent is not attempting to spoof the sender email address (they use the compromised hotel's email address) but they simply change the display name of that address, which the email protocol allows you to do.
Display name is the human-friendly name of a particular email address. An
example would be "WebHotelier Bookings" <bookings@webhotelier.net>
Most email clients simply display the friendly name instead of the full
email address (in the above example, just "WebHotelier Bookings").
This makes it a useful phishing attack method.
The phishing emails use "WebHotelier" or "primalRES" as the display name, however if someone checks the sender's emails address they will find that it originated from a domain unrelated to us. A real example from a phishing attempt:
From: WebHotelier <info@pliadongi.gr> Date: Thu, 15 Aug 2019 at 13:47 Subject: You have a new reservation [5713975753] made through booking.com.
In addition, the content of the emails is targeted to real hoteliers that are used to receiving this kind of messages. Thus, it is more likely an unsuspected user might click and download the malicious content.
Protection measures:
The display name of any email is easily spoofed, so the golden rule against phishing attempts is:
Always check the sender's domain
- Confirm the sender’s identity before replying to email requests and before opening attachments or clicking on links, even if they appear to come from a legitimate source.
- We always send emails from @webhotelier.net. Customers that use our channel manager also receive emails from @primal-res.com.
We urge caution and remind you of simple precautions you must take
- Consult your IT department about any phishing attempts.
- When unsure, call us to validate communications are originating from us.
- Create a filter on your email assigning emails received from @webhotelier.net or @primal-res.com to a specific folder/label.
- If you receive an email from any other address DO NOT OPEN it and certainly do not click on any links that it contains.
What should you do if you clicked on a link and run the malware:
Primary actions
- Shut down your computer immediately.
- Inform your IT department.
- Contact us.
Secondary actions
- Turn your computer back on only if disconnected from the Internet.
- The infected computer should NOT be part of your local network either. It might infect neighbouring computers. If the computer connects automatically via WiFi, turn off your router while you clean up the damage.
- Immediately change your email passwords.
- Check your mail server logs for unauthorized activity. Warning! Your email client (e.g. Outlook) will probably have all malicious tracks wiped, therefore it might look that nothing has happened.
- If the affected system is a personal computer, consider formatting and re-installing your software. Warning! Running your antivirus might not be enough!
- If the affected system is a server computer, a full security audit of your computer systems and network is recommended.
Summary:
- Always check the domain address of the sender.
- Contact your IT person if you encounter suspicious activity.
- If you encounter and identify a phishing email, immediately mark it as spam or delete it.
Thank you in advance for your attention.